
[ This article was originally published here by Indusface.com ]
With everyone living online these days, web traffic to the online channels is on the upsurge. However, if you delve into the traffic, you’ll see that most of the traffic is not from legitimate users. Only less than half of the traffic is actual humans, the rest are bots including both good and bad bots.
In the early days, the bots were used only for spamming or small scraping attempts. Today, bot operators are taking advantage of automation at scale to perform malicious activities. Such activities include taking over user accounts, abusing APIs, performing DDoS attacks, scraping unique pricing information, competitive data mining, web scraping, digital fraud, financial data harvesting, transaction fraud, brute-force login, and many more.
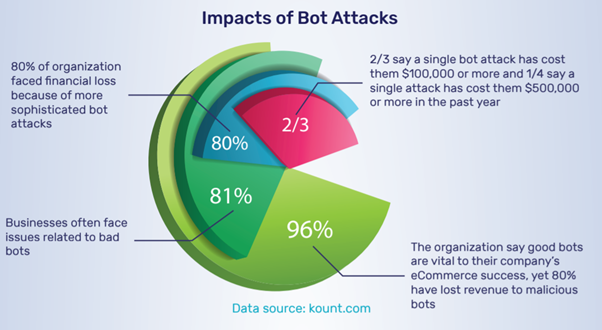
Despite serious impacts, are organizations adopting an effective bot management approach? The answer is, No.
Many businesses are still trying to block bots with traditional solutions, putting security at risk. So why does the traditional WAF approach for bot mitigation fail?
Let’s look into the reasons behind the failure of WAF in bot management and the benefits of Advanced WAF protection.
Why Is Traditional WAF Protection Inadequate?
To understand the importance of Advanced WAF for bot detection and mitigation let’s explore the common security measures taken by businesses to block bot attacks and why they’re ineffective.
- Code-Level Security – this practice implements security at the initial stage of development rather than regretting it at the end of the life cycle. However, this basic security level is not adequate to block today’s evolving bots as they perfectly mimic human users. This practice also lacks the capability of fraud intelligence against bots patterns.
- Traditional IP Blocking – if a company wants to block a subset of traffic to their website, IP blocking is one of the most effective methods. With evolving fraud patterns, this method is not adequate for all scenarios. Blocking IP may sometimes end up blocking the legitimate users using the IP.
- Traditional Web Application Firewall – WAFs are primarily designed to protect the website and web applications against attacks like SQL Injections, XSS (Cross-site scripting), Session Hijacking, Cross-site request forgery, and other web attacks. Most of the web application firewall is inadequate to match with the changes of the user profiles and apps, which undergo continuous change.
Though Next-generation firewalls (NGFW) claim to be application-aware, they still rely on basic bot mitigation capabilities like blocking IPs, users generating repetitive requests, or fingerprinting the browsers. They examine the first few bytes of the payload, as a result, next-generation bots, which use modern techniques remain undetected.
The WAF technologies undergo several improvements, but it depends on the filter-based approach to detect malicious payloads that have proven inadequate against blocking bots and other automated threats.
Further, managing WAF policies compiled with operational complexity has caused several companies to leave web apps unprotected. In several cases, a known vulnerability was exploited because the targeted enterprise couldn’t patch the vulnerabilities quickly enough.
Combining these challenges, the easy availability of bots for hire and innovations in automation technologies has made bot detection and mitigation much harder.
To deploy effective bot management and protection, organizations need Web application firewall technology, which evolves and fine-tunes itself automatically to detect the most sophisticated bots and delivers continuous security. The good news is, Advanced WAF employs effective measures to detect and stop evolving botnets.
Benefits of Advanced WAF Protection in Bot Management
In the case of Advanced WAF protection, the combination of WAF technology and behavior analysis, which detects malicious bot activity makes it easier to spot bot traffic without human intervention.
Bot detection of Advanced WAF includes components like:
- Custom rules for bot mitigation
- Spots the bots based on the behavior of past traffic and blocks them
- Close to zero false-positive which in turn ensure legitimate traffic is not blocked
With proactive bot defense, advanced WAF tracks attackers beyond their IP address detects the nature of the user, and differentiate legitimate bots from a malicious one. It also eliminates the impact to the UX (User Experience) connected with CAPTCHA challenges.
Besides the out-of-box fully managed WAF features that block attacks, companies can create their own custom policies and rules to block bot attacks, which they’re receiving or that they fear they may receive.
For instance – it is possible to make a rule to block access to the password reset request on the website if repetitive requests are made from the same IP within a short span.
With a threat intelligence database, which holds details of all the recent attacks, associated IP addresses, locations, whether those attacks were machine or man generated. This database is updated all the time. If any request is made from any suspicious IP address, that address will be blocked automatically.
Comparing Traditional WAF with Advanced WAF
| Security Capabilities | Traditional WAFs | Advanced WAF |
| Protection from OWASP Top 10 Vulnerabilities | Yes | Yes |
| Protection from Simple bots | Yes | Yes |
| Customized actions against suspicious bot types | No | Yes |
| Collective bot intelligence (behavioral patterns, fingerprints, & IP) | No | Yes |
| Risk of false positives | High | None |
| Detection of sophisticated bot attacks | No | Yes |
| Mitigation of dynamic IP | Limited | Yes |
| Fingerprinting of malicious devices | Yes | Yes |
| HTTP Traffic Inspection | Yes | Yes |
The Closure
Web applications are targeted around the clock and the hackers are figuring out new ways to breach the website and cause chaos. Onboarding fully managed cloud-based WAF, you are not only reducing the risks of botnets but also minimizing the processing loads on your infrastructure by blocking malicious bot traffic.






















