
Adoption of cloud services, whether consumed as 3rd party services provided by various vendors or in the form in-house developed software and/or services leveraging Platform-as-a-Service (PaaS) from major Cloud Service Providers (CSPs) has been steadily on the rise in critical infrastructure (CI) related industries[i]. This represents a significant shift for such industries which have traditionally relied on isolation via air-gapped networks. The “move to cloud” presents significant cybersecurity challenges for critical infrastructure related industries, that still put a premium on one element of the C-I-A triad (confidentiality, integrity and availability) over others, namely availability[ii].
What further compounds an already complex architectural and security landscape is the fact that critical infrastructure industries in various countries tend to be either partially or fully government controlled; with many providing “essential services” such as Healthcare, Water, Power, Emergency Services and Food production.
Impact to “essential services”
The US Government’s Cybersecurity and Infrastructure Security Agency or CISA lists about 16 industries that it considers as falling within the ‘critical infrastructure’ umbrella, including several which can be considered as “essential services” including transportation sector, water sector, food and agriculture sector, healthcare and public health sector, chemical sector, dams sector, energy and utilities sector (E&U), emergency services sector[iii]. UK’s CPNI agency also lists about 13 sectors or industries which have a significant overlap with the US list, with several industries offering essential public services directly (such as Water, Food, Health)[iv].
Cyber threats from rival nation states and rogue actors are very plausible and are also becoming increasingly common owing to the geopolitics of the current era. This has in several cases, resulted in loss of continuum of public services that are offered to common citizens.
- In an example from last year, lack of risk-based adoption of cloud software and lack of controls to prevent access to ICS networks caused service disruption at a US drinking water treatment facility, where cyber-attack via poorly controlled cloud software (desktop sharing) had increased sodium hydroxide levels in drinking water[v].
- In another example from this year, a version of the Industroyer malware that spreads via spear phishing emails which are part of cloud-based email systems, got access to power grids and almost shut down power supply to a portion of Ukraine’s capital (lack of or poor implementation of cloud native controls to detect and avoid phishing). This attempt had actually succeeded back in 2016, and remains a potent threat[vi].
In short, essential services affects us all and any disruption will tend to impact the way we carry out our daily tasks, not to mention the significant economic costs associated with them.
Current Security Landscape of Critical Infrastructure Industries
Cybersecurity is relatively still very new within CI sectors, which is traditionally lower down the priority list for many these organizations. Critical infrastructure related industries have certain things in common, which in spite of the extreme diversity of their product or service offerings, ties them together:
- Industrial Control Systems (ICS) or OT Systems
These industries variously and extensively use ICS systems such as Supervisory Control and Data Acquisition (SCADA) systems, Distributed Control Systems (DCS), Programmable Logic Controllers (PLCs), smart transformers, smart grids, Remote Terminal Units (RTUs) and other such systems.
ICS systems are integral to CI industries, and form the backbone of all their facilities (except corporate offices) such as plants, refineries, workshops, substations etc. These systems are traditionally air-gapped from the corporate and external networks based on the Purdue Reference Model.
- Purdue Reference Model
Most industries in CI, at least on theory try to align their networks and operations to the Purdue reference model. The Purdue reference model separates various operations and functions into loose logical swim lanes across the enterprise[vii]. There are hierarchical divisions on the basis of which a network is built.
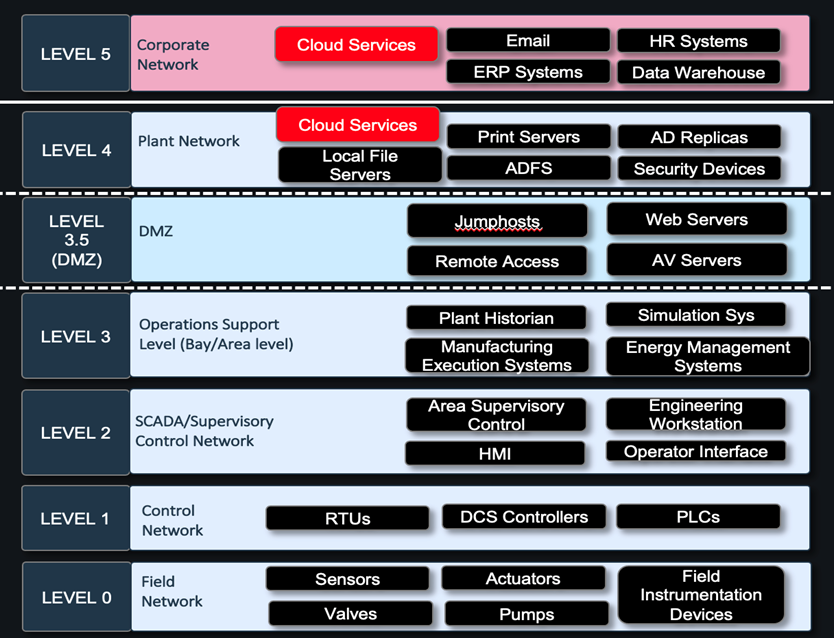
- IoT sensors and devices
Most plants and facilities have a high degree of IoT sensors and devices communicating wirelessly using very specific protocols, and very often interacting with cloud-based services for receiving and providing different telemetry data.
These unique characteristics of these industries present unique challenges from a security standpoint:
- Lack of Risk Based decision making when adopting cloud services
Cloud services are adopted to meet specific requirements such as a third-party assessment tool, GRC tool, tools for corporate segmentation etc. Risk assessments including understanding of threat vectors due to introduction of new technologies is not typically or adequately addressed.
- Using Purdue model for segmentation as a gold standard
Purdue model served the need for logical enterprise architecture for decades until the proliferation of IoT devices, cloud services and myriad of other enterprise-wide software and tools. Specifically in E&U industry, smart grids and smart transformers present a challenge that is not neatly addressed by Purdue model (by definition smart devices are IoT enabled devices that have cloud connectivity beyond the control networks)
- Lack of robust segmentation and micro-segmentation practices
Most networks have devices that are traditionally sold by automation vendors such as Rockwell, Honeywell, Mitsubishi, Yokogawa etc., which come with defined enterprise network architectures focused on optimum deployments and performance of their equipment. This makes implementing best practices around segmentation within ICS networks very challenging owing to interoperability of solutions, especially with the penetration of cloud services
- Ubiquitousness of Legacy Devices
Legacy devices exist in ICS networks, and depending on the organization and industry they operate within, their percentage varies. Upgrading these legacy devices are often complex projects that are not necessarily undertaken, given the extreme importance placed on ‘zero downtime’.
- Overreliance on perimeter firewalls and industrial IDS tools
Several industrial IDS tools that perform deep packet inspection of traffic have proliferated the market. Organizations have been confusing deployment of IDS tools that only indicate anomalous activity as equivalent of securing networks. Additionally, perimeter firewalls are heavily relied upon with little importance to lateral firewalls
A holistic cyber security program focused on cloud and third parties to improve security preparedness
There is no silver bullet when it comes to addressing security concerns within CI industries that provide essential public services. It is impossible and counter-productive to stop the proliferation of cloud services within corporate and even ICS environments. But also, to ignore the security challenges they pose is akin to burying one’s head in the sand, since this is a clear and present threat. Some of the best practices to consider in designing robust networks and enterprise architecture for public services industries are the following (by no means an exhaustive list):
- Comprehensive security program that addresses all domains of cloud security[viii]:
Establishing a comprehensive cloud security program that consists of all domains such as Access Control, Communications Security, Data Security, Threat Modeling and so on focused on adoption of newer cloud technologies is imperative. This should also be backed by a governance program that proactively addresses security as it pertains to cloud services/software being brought in.
- Risk Assessments of all 3rd party cloud services and also PaaS services:
Performing a thorough risk assessment on a component-by-component basis to determine risk before any product is brought into the network is imperative. Threat modeling to ensure various threat vectors have been assessed and the risk has been quantified, will mitigate some of the risks
- Security controls, not just at the perimeter, but spread across ICS networks
Securing ICS networks doesn’t just involve perimeter security, but a whole range of security controls that the security program must implement, including lateral segmentation, possibly micro-segmentation, device level security, and device access control. Special controls must be in place for IoT devices as well. Overreliance on IDS tools doesn’t help the case, as the mitigation strategies still need to put in place.
- Purdue model by itself will not cut it any more, it needs to be revamped for a cloud world
Though Purdue model will continue to provide the foundation on the basis of which CI public service organizations will operate, a more hybrid model that takes into account the reality that IoT devices and cloud services don’t necessarily interact with devices based on logical or abstract boundaries in important. Knowing data flows including API calls within and outside of the networks is very critical to come up with the best segmentation strategy
It is not particularly difficult to list out ad-nauseum the best practice recommendations for cloud adoption to minimize disruption within CI industries that provide essential services. The fundamental point is that cloud is here to stay and grow in areas that make economic sense for organizations. Also, there is a gradual blurring of lines between corporate and ICS networks, which will only accelerate in future. How organizations prepare themselves to effectively react to security challenges that arise out of it, in an age of extremely volatile geopolitical happenings is what will determine whether essential services are sufficiently protected from remote (cyber) disruptions or not.
[i] https://icscsi.org/library/Documents/ICS_Vulnerabilities/DHS-OCIA%20-%20Risks%20to%20Critical%20Infrastructure%20that%20use%20Cloud%20Services.pdf
[ii] https://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-82r2.pdf
[iii] https://www.cisa.gov/critical-infrastructure-sectors
[iv] https://www.cpni.gov.uk/critical-national-infrastructure-0
[v] https://www.cisa.gov/uscert/ncas/alerts/aa21-042a
[vi] https://www.cisa.gov/uscert/ncas/alerts/aa22-110a
[vii] https://www.sans.org/blog/introduction-to-ics-security-part-2/
[viii] https://www.cisa.gov/sites/default/files/publications/Cloud%20Security%20Technical%20Reference%20Architecture.pdf





















