
Author: Nick Gicinto, Vice President, Incident Investigation & Intelligence (i3) at RiskIQ
In the wake of the tragic events that unfolded on Capitol Hill on January 6, 2021, it is now clear that abundant warning signs existed to alert lawmakers and law enforcement that a dangerous storm was brewing. It is uncommon for threats of this nature to be so blatantly forecasted. Yet, not enough people did. On December 21, 2020, writer and political analyst Arieh Kovler tweeted, “On January 6, armed Trumpist militias will be rallying in [D.C.], at Trump’s orders. It’s highly likely that they’ll try to storm the capitol after it certifies Joe Biden’s win. I don’t think this has sunk in yet.”[1]
Now that so much of the world has turned to social media, and with the proliferation of so many various platforms, it has become increasingly difficult to monitor where threats broadcast themselves, particularly when so many discovery platforms are keyword based. If a threat actor makes a post that slips past your keyword threat matrix, it will slip through your detection. Your security teams and corporate leadership will be caught off guard by the threat you will later discover was forecast right in front of your very eyes. It didn’t pop up out of nowhere; unfortunately, you just missed it.
In just the past few weeks, the US Capitol was physically breached by individuals whom many in the US Government are calling insurrectionists. Meanwhile, the data within servers of countless companies and many US Government agencies was swallowed up in the wake of the SolarWinds breach. Let’s not forget the number of corporate breaches, ransomware attacks, and other cyber events that seemingly occur on a weekly basis these days.
The US has seen an unprecedented level of incursion into its most protected institutions, and while we’re still dealing with the fallout from these events, we will undoubtedly and sadly see more cyber intrusions and physical attacks occur. Whether we are able to stay ahead of these future incidents is another story.
A post on social media platform Parler following the Capitol Hill incursion on 6 January 2021. This user suggests that followers should engage in violence against Democrats and tech company executives.
If You Can’t See the Entire Web, You Can’t See Anything
Corporate security and intelligence teams know that threat actors wish to use the platforms where their message can reach the most people. Thus, by keeping their focus on major platforms such as Twitter, Facebook, Instagram, and the like, security and intelligence teams are likely to catch the majority of the physical threats directed at corporate America and the US Government. However, as we are now seeing Twitter stamp out QAnon followers from it’s platform, and Parler received notice from Amazon that it will no longer host its platform on its servers, these groups will be forced to turn to lesser-known platforms for their communications, planning, and threats.
According to LifeRaft, a threat intelligence platform provider, many Parler users are now moving over to Gab.com, a social media platform “known for openly accepting the kinds of rhetoric denounced by other social media and big tech companies, under the notion of free speech and the First Amendment Right of the US Constitution.”
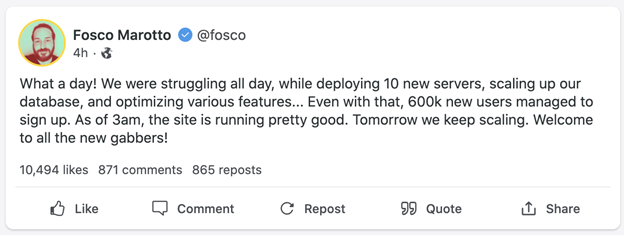
A post on social media platform Gab describes onboarding 600,000 new users in one day, as observed by LifeRaft’s Navigator.
Gab.com is commonly recognized as the platform where the suspected Pittsburgh synagogue shooter, Robert Bowers, published anti-Semitic comments before he allegedly killed 11 people and wounded many others at the Tree of Life synagogue.”
Current Approaches Aren’t Good Enough Anymore
Where companies could previously get by with basic—or even free— tools for monitoring, this scenario underscores the importance of having internet-wide visibility in order to maintain a handle on where threats persist across cyberspace. Whether the threat is cyber or physical in nature, threats originating online are real, and as more and more users migrate to lesser-known corners of the internet, the dark web, end-to-end encrypted platforms, and FTP sites for downloading information, corporate security teams will find themselves in the dark when it comes to maintaining visibility into them.
Corporate security and intelligence teams often rely on social media monitoring feeds, proprietary data, news tickers, data from their SIEM or endpoints, as well as industry-specific intelligence they may subscribe to in order to stay on top of emerging trends and relevant security threats. Some of their data feeds may include open source scrapes of websites, social media collection from varied sources, some deep web coverage of forums and blogs, paste sites, and possibly some dark web collection. Rarely do they find all this information in one place. Rather, they often turn to multiple tools which typically do not share information or talk to one another.
Threat Intel is Only As Good as How It’s Correlated
Evaluating these systems for their ability to surface real events of interests or threats takes time, patience, and skill. However, the real trick is tying all of that information together in a way that gives security teams actionable intelligence that is timely and relevant, and further requires subject matter expert analysts to make sense of what their data collection is telling them. They will typically triage these events, seek to corroborate what they are seeing, and if deemed credible, they will escalate the information up the chain for leadership awareness.
Typically, their data sources are static. The collection they have is what they have. When threat actors move to new platforms these teams may not even know that a transition has occurred, especially if they are dealing with so much data they cannot manage their visibility authoritatively.
Most commonly, the signal goes silent or dark. If this loss of signal is detected, the analyst must now evaluate what it means. Is the threat gone or mitigated? Is the silence accidental or purposeful? Or, did it move to another medium where the team does not have coverage and thus has no ability to track the threat? This should be a concern of law enforcement and corporate security teams as these groups are squeezed tighter and tighter in the wake of the response to the Capitol building incursion.
Handling the Next Attack
How do teams stay ahead of the curve? Security teams must ensure they possess the tools and expertise to maintain internet-wide visibility and they are not afraid to spend proactively to prevent threats. There are tools that exist, such as LifeRaft’s Navigator, that provide visibility across lesser known platforms, and these vendors stay on top of emerging technologies and methods of communication, and incorporate that collection into their datasets at the pace of helping companies stay proactive against threats from both the cyber and the physical realm.
Companies also need to be keenly aware of what their attack surface looks like to threat actors. This understanding is critical to getting ahead of potential gaps in corporate security posture from a cyber, data, and physical security standpoint. The expertise to manage that data is just as important, and companies who endeavor to stay ahead of the game, protect themselves from these threats, and hope to avoid picking up the pieces after an attack has occurred will need to hire the right level of talent—trained intelligence experts—to operate these tools and maximize their intelligence value.
The next Capitol Hill-like scenario, especially according to the threats made on multiple platforms over the previous few days, could occur in the not too distant future, and just not against US Government targets. The question is whether the US Government and companies which find themselves in these crosshairs will have the necessary visibility to see their attackers coming ahead of time.
Nick Gicinto, Vice President, Incident Investigation & Intelligence (i3) at RiskIQ
Nick Gicinto is currently the Vice President of Incident Investigation & Intelligence (i3) at RiskIQ, the World Leader in Attack Surface Management. Nick developed RiskIQ’s i3 team along with growing the Executive Guardian platform, a world-class threat detection and management platform aimed at protecting company personnel from both digital and physical threats around the globe. Prior to joining RiskIQ, Nick developed and led Insider Threat, Intelligence, and Investigation programs for Tesla and Uber in the United States. He served in the US Intelligence Community for 10 years prior to joining the private sector. He holds a master’s degree in Defense & Strategic Studies from Missouri State University and is currently an Adjunct Professor of Political Science at William Jewell College, his undergraduate alma mater.
[1] https://twitter.com/ariehkovler/status/1341016471795843080?s=20



















