
By Keir Finlow-Bates, passionate blockchain enthusiast and technologist, Resonance Security
TL;DR — do not deploy smart contract code that you do not understand, and do not send tokens or ETH to contracts that are not managed by an entity that you trust.
I can’t believe that trading bot scams on Ethereum and Ethereum-like chains are still going on. But they are. Today I had to deliver the bad news to someone that they had lost a significant amount of ETH to such a trading bot scam. And unfortunately, YouTube, Telegram or Discord, and Remix aren’t doing much to prevent them.
These scams have been going on for years now, and people are still falling for them.
The core of the scam consists of:
1. some Solidity code that the scammer claims is a trading bot smart contract that will make you money while you sleep, and
2. a tutorial video showing you how to deploy the smart contract using Remix
The reason the scam works is because in crypto there are people who don’t have enough underlying technical knowledge to determine that what it promises is nonsense or assess the code competently to see that it is designed to steal your crypto-assets, but they do have enough technical knowledge and confidence to follow the instructions given.
They also often made significant profits by buying crypto earlier on, making them excellent targets.
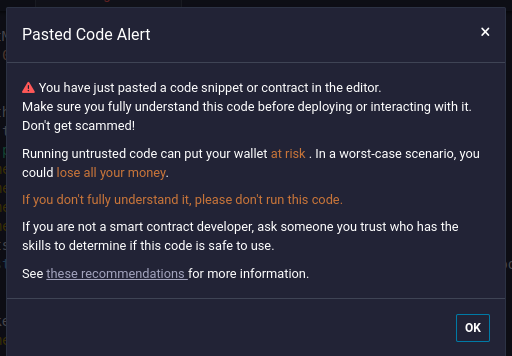
What part does Remix play?
Remix is an online tool provided by the Ethereum Foundation, which allows you to write, debug, and deploy smart contracts from your browser.
Remix warns you about trading bot scams on its front page, but the warning is easily overlooked, as the main screen is full of moving adverts for projects, templates for contracts, and other distracting information.

- Make it look like the contract has something to do with a token-swapping contract like Uniswap or Pancakeswap by including imports of one of those contracts at the top of the code. Clue #1: the functions in these imports are never called.
- Include lots of comments that make it look like the functions are for finding instances of the swapping contracts. Many of these functions aren’t even called anywhere in the code. Clue #2: the comments are technobabble.
- Use obfuscated code blocks in nested misleadingly named functions to construct the scammer’s address. Clue #3: running these functions always returns the same value.
- All publicly callable functions in the contract contain a transfer of the ETH (or chain native cryptocurrency) balance of the contract to the scammer’s address. Clue #4: the transfer code has no comments.
Lessons learned
The aphorism, “If it seems too good to be true, it probably is” holds everywhere, even for crypto. The problem with crypto is that many people have made a lot of money by buying low in a way that seems too good to be true, and that softens them up for scammers to come along and relieve them of what to many seems like not-so-hard-earned cash.
I’ve personally lost 0.1 BTC and about 3 ETH to scams over the last decade. It’s nothing to be ashamed of, but it is something to be angry about. And it does teach you to be more careful.
The key thing is to avoid acting on that irrational initial impulse that combines the emotions of fear and greed — fear that you’re going to miss out if you don’t strike while the digital iron is hot, and greed for the possibility of making easy money.
Instead, look at the offer being made rationally.
Does it make sense that someone who has invented a trading bot that can turn 3 ETH into a perpetual stream of 6 ETH every week would spend a fortune making a video explaining to total strangers how they can do it too? What would they gain from that? Is it even possible to have a system where, no matter how many people join, magical internet money will flow to all of the participants?
No, of course it doesn’t make sense.
It’s as crazy as believing a tweet that if you send Bill Gates one bitcoin or Vitalik Buterin one ETH, he will send you two back. And here’s his Bitcoin or Ethereum address.
Except … people have fallen for that scam too.
[This article was written by Keir Finlow-Bates, a passionate blockchain enthusiast and technologist, who represents Resonance Security]





















