
By Motti Elloul, VP Customer Success and Incident Response, Perception Point
Email phishing scams are nothing new. But they are growing increasingly prevalent and sophisticated – over 3 billion phishing emails are sent every day, and the tactics used to disguise them are only growing more devious.
One case in point: the Incident Response team from our company, Perception Point, recently discovered a new phishing campaign that uses HTML files to conceal malicious scripts, duping unsuspecting users into entering their credentials and divulging sensitive personal data.
This latest attack strategy underscores the importance of email security, acting as the first line of defense, and emphasizes how comprehensive solutions are required to detect and remediate extremely deceptive threats that arrive in enterprise users’ inboxes. These solutions can help take the onus off of employees, reducing the possibility of human error, though naturally they still must exercise general caution.
How the Attack Works
In this newly identified phishing scam, an attacker sends an email disguised as an urgent company-related payment request with an HTML attachment. Upon opening the HTML file, the user is redirected to a spoofed Microsoft login page, where they are prompted to enter their credentials.
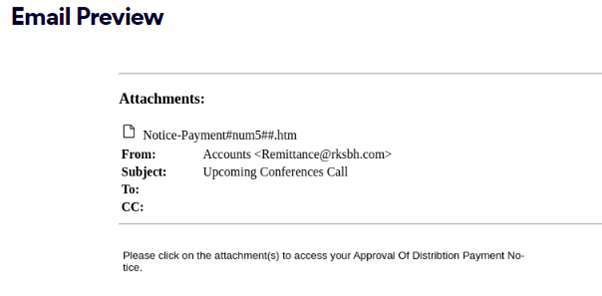
Although this attack may seem like a typical phishing model, it is perhaps more clever than meets the eye, as it is capable of bypassing advanced detection methods and here’s why.
When standard email security systems scan the HTML attachment, the only thing they typically lay bare is the Base64 encoded object. However, when running the attachment through Perception Point’s solution, dynamically scanning 100% of content that other platforms may overlook, it was discovered that once decoded, the object led to a SVG file encoded as a URL. Only upon decoding the file for a second time was an obfuscated script intended for credential theft exposed.
Pulling Back the Layers
Diving into the code, researchers on the Incident Response team managed to locate the source of the uploaded CSS as well as the obfuscated script on the URL that is meant for credential stealing. By going through each step of the attack, the team was able to obtain the first URL used in the script to determine where the payload was sent as well as its delivery method: they discovered that the attack was designed to send a POST request to the extracted URL before sending the victim’s credentials as a JSON (JavaScript Object Notation) format file.
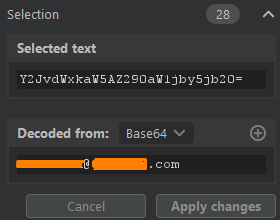
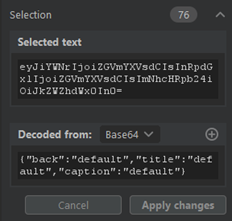
Researchers further found that the variable marked ‘b’ in the attack had all the CSS base64 encoded. After delving into a few more decoded variables, the researchers discovered the HTML of the login. They then determined that at this point in the attack, the hacker would use a script for stealing the entered credentials utilizing a Base64 encoded “btype” variable. Although the URL address was revealed to be slightly incomplete after a round of decoding, researchers saw that the script would compensate by adding the letter ‘h’ to complete it. This made it suitable to host an obfuscated script with the expressed purpose of credential stealing.
Though the sophistication of this attack is alarming, there are likely countless others like it. Unfortunately, the majority of email security systems lack the capacity to peel back these complex layers.
Catch the Phish
There’s no telling how much more elusive these phishing threats will become – this newest attack campaign certainly won’t be the last of its kind. In fact, according to Perception Point’s latest Cybersecurity Trends Report, advanced phishing attacks skyrocketed by 436% in 2022.
While it still is good practice for employees to approach their email-based processes and tasks with caution and scrutiny, it is in their organization’s best interest to proactively deploy multi-layered security solutions such as those that harness image recognition technologies to detect even the subtlest of phishing scams. Organizations enjoy immediate support in preventing and remediating attacks by integrating incident response services into their cybersecurity solutions, effectively countering perpetrators of phishing attacks.





















