
Adam Meyer wrote an interesting post about How to Make Threat Intelligence Practical for Your Organization that I would like to share.
“f there is a drumbeat I will continue to harp on it’s the importance of practical cyber threat intelligence. With so much data out there, and so much confusion in the market as to what intel even is, intel’s practicality takes on even greater significance.
One key aspect of making threat intelligence practical is to ensure the intel is evaluated. What do I mean by this? Well, there are a lot of threat intelligence misconceptions that have to do with automation and speed. Threat intelligence feeds or platforms that provide data or indicators of compromise (IOCs) are delivering a first step toward intel, but the practicality of it is questionable at best. For example, if it’s presented in “real-time”, then it is most definitely NOT intel. It is data/information that has not been evaluated and therefore known to have occurred.
What is Evaluated Threat Intelligence?
Evaluated threat intelligence is the concept of all threat data being reviewed and confirmed. It is standardized and organized in an easy-to-consume way so analysts can begin their work from the 50 yard line instead of from their own 10.
If the data is delivered in real-time, but isn’t validated, or in a context that is useful for your organization, you need to assign your own analysts to conduct that intel work. It’s a question of who takes on that burden of effort. Even if the indicators or data are known to be true, are they relevant to your organization and technical environment? Actionable is a term thrown around a lot in our industry but if the data isn’t evaluated and relevant to your organization, it’s ultimately creating just a lot of actions for you that may or may not be a wise allocation of money, resources, and time. Again, this goes back to the practicality of the “intel” handed to you.
As someone who runs an intelligence team, having evaluated intel at my fingertips instead of raw data gives me more to work with right off the bat. I don’t have to sift through false positive after false positive to get to the good stuff. I can rack and stack what is important to me for the day and spend my effort on changing an outcome for the better.
While every organization has varying levels of cyber threat intelligence maturity, most I’ve come across lack trained staff and resources. Yet they want to have intel help drive the bus so to speak. While bringing in threat data feed(s) may sound great in theory, without the personnel to handle it, you’re setting yourself up for disappointment. This is another example where evaluated intel can help.
Finished Intelligence that is Practical and Usable
Another area of focus on making your intel practical is with finished intelligence. Intelligence needs to be useful, relevant, and timely – and the only way to accomplish that is to send it through an evaluation process. What’s the situation? How many threats are active? How can a threat harm my organization? And most importantly, what do I do about it?
Finished intelligence requires evaluation and analysis of malicious actors’ capability, opportunity, and intent. It goes beyond an indicator or even a set of indicators (While an IOC may add detail, it must still be researched, analyzed and put into context). Intelligence is not a platform, data feed or tool – it’s a capability. It requires human analysis and should include educated assumptions with assigned confidence levels, along with evidence and rationale as support. It must be specific to your organization to ensure its value and significance. And it must include mitigation recommendations, e.g. “what do I do with this?” No one likes being told about problems without being given potential solutions.
Finished intelligence can be delivered in several different outputs, with the most favored output determined by the end user:
• At any or all of the varying levels of intel – from tactical to operational to strategic
• Via an informal conversation and/or formal cyber risk briefing
• Via a formal email alert and/or in-depth report
• Via interactive dashboards
Regardless of the format the finished intelligence is delivered, if it doesn’t tell you your risk and how to mitigate it, it isn’t really fully usable or practical.
“Just shoot me straight”, “what’s the problem?” or “cut to the chase” are phrases I use all the time. Your decision makers use them too – they may not use those exact phrases but they ultimately want to quickly get to the punchline. Finished intelligence should be viewed in the same vein. It needs to get to the point so the end user does not have to hunt for an answer or spend lots of time peeling back layers of the onion.
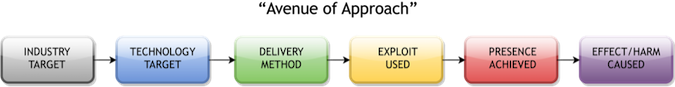
My intel team focuses on the “avenue of approach” methodology (shown above) for the sake of getting to that punchline quickly. It is a model that lays out the industry target, the technology target, the delivery method, the exploit used, the presence that is achieved and the effect/harm caused. This methodology allows us to present the finished intelligence at any level necessary (strategic, operational and/or tactical) so it can be used across different groups in the organization. Knowing how an adversary is looking to attack you (based on what has happened to other, similar organizations – evaluated intel, what we know to be true) helps identify areas of risk to shore up and also sets the stage for recommendations on what to do about that threat.
To sum up, practical threat intelligence goes beyond IOCs, data streams and information sharing. It concisely gives you the story and the conclusion. To get there, push on your own intel teams as well as your external vendors to not only tell you something important that you didn’t already know, but what steps to take to ultimately close that risk in an evaluated, efficient, easy-to-consume manner. “
—–
Source:
www.securityweek.com/how-make-threat-intelligence-practical-your-organization
Photo: seeetech.com





















