
The INCIDENT RESPONSE REPORT is a unique opportunity for cybersecurity marketers to receive fact-based thought leadership content, quality leads, and brand visibility in the cybersecurity market.
Based on a comprehensive survey of cybersecurity professionals in our 500,000 member cybersecurity community, the report will reveal the latest trends and challenges in incident response, why and how organizations invest in it, and the security capabilities companies are prioritizing.
Complete the form on the right to receive more details, including sponsorship packages and pricing.
Incident response is the methodology an organization uses to respond to and manage a cyberattack. An attack or data breach can wreak havoc potentially affecting customers, intellectual property company time and resources, and brand value. Incident response aims to reduce this damage and recover as quickly as possible.
Based on a comprehensive survey of cybersecurity professionals in our 500,000 member cybersecurity community, the report will reveal the latest incident response trends and challenges, why and how organizations invest in incident response, and the security capabilities companies are prioritizing.
[ Please contact us to review the survey questions and suggest your custom survey questions ].
The report presents a unique opportunity for security vendors and service providers to educate buyers and provide credible, third-party validated marketing content:
- Receive fresh, unique, third-party validated thought leadership content on cloud security trends, challenges and solutions. Customize the report to fit your brand, marketing message and budget.
- Deliver custom-branded thought leadership content, generate leads for your sales team, and raise visibility for your brand in the cybersecurity market.
- Engage buyers with fact-based content including insightful benchmark data and user opinions. Use the asset on your website, as part of lead generation campaigns, for your sales team, content syndication campaigns, on social media, PR, and more.
- Educate IT decision makers on the benefits of cybersecurity solutions and incorporate your point of view as the answer to their security challenges.
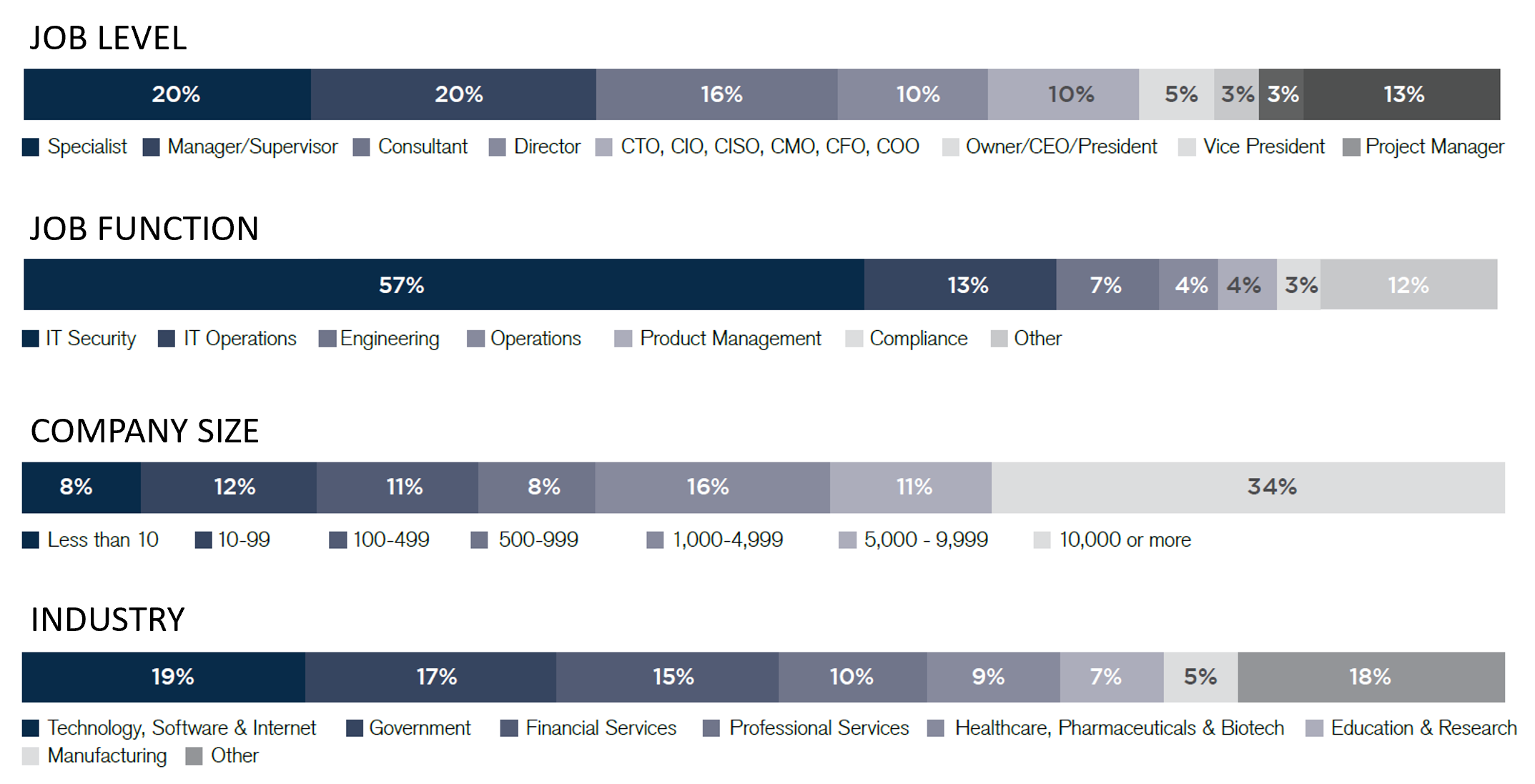
Our survey reports are based on a comprehensive online survey of cybersecurity and IT professionals active in our 500,000 member information security community, reflecting a representative sample and cross section of roles, company sizes, and industries.
The research report program is based on a comprehensive online survey of professionals in our 500,000 member cybersecurity community. The process is designed to ensure the highest quality research, measurable marketing results, and a superior sponsor experience:
- Interview with you to confirm objectives and draft an outline of the survey instrument, including custom survey questions.
- Creation of the survey instrument (typically between 15 and 30 questions, depending on the topic), including custom questions to impart your unique market focus and point of view.
- Administration of the survey process, including collection of survey responses from the cybersecurity panel and quality assurance. All research is based on a comprehensive online survey of cybersecurity professionals (minimum sample of 200).
- Analysis and interpretation of the survey results and application of any filters, cross tabulation, year-over-year comparisons, etc.
- Creation of report content, including research findings, charts and graphic design to bring the survey results to life in a compelling report.
- Work progress is shared with you at every milestone. This way, you can review and provide feedback on the survey and report content – until you are satisfied with the outcome.
- Publication of the final research report as part of a comprehensive marketing, PR, and social media campaign (promotion and additional content syndication, lead generation, webinar programs and infographics can be added to your custom package).
We provide a unique, no-risk, money-back guarantee for report clients.
- Final invoice is not sent until the research report has been published.
- If you are not completely satisfied with the final report, we will not invoice you. No questions asked.
- You can decide when you want to be invoiced to align with your budget cycle, giving you more financial flexibility.
- OVERVIEW
-
Incident response is the methodology an organization uses to respond to and manage a cyberattack. An attack or data breach can wreak havoc potentially affecting customers, intellectual property company time and resources, and brand value. Incident response aims to reduce this damage and recover as quickly as possible.
Based on a comprehensive survey of cybersecurity professionals in our 500,000 member cybersecurity community, the report will reveal the latest incident response trends and challenges, why and how organizations invest in incident response, and the security capabilities companies are prioritizing.
[ Please contact us to review the survey questions and suggest your custom survey questions ].
- BENEFITS
-
The report presents a unique opportunity for security vendors and service providers to educate buyers and provide credible, third-party validated marketing content:
- Receive fresh, unique, third-party validated thought leadership content on cloud security trends, challenges and solutions. Customize the report to fit your brand, marketing message and budget.
- Deliver custom-branded thought leadership content, generate leads for your sales team, and raise visibility for your brand in the cybersecurity market.
- Engage buyers with fact-based content including insightful benchmark data and user opinions. Use the asset on your website, as part of lead generation campaigns, for your sales team, content syndication campaigns, on social media, PR, and more.
- Educate IT decision makers on the benefits of cybersecurity solutions and incorporate your point of view as the answer to their security challenges.
- DEMOGRAPHICS
-
Our survey reports are based on a comprehensive online survey of cybersecurity and IT professionals active in our 500,000 member information security community, reflecting a representative sample and cross section of roles, company sizes, and industries.



- METHODOLOGY
-
The research report program is based on a comprehensive online survey of professionals in our 500,000 member cybersecurity community. The process is designed to ensure the highest quality research, measurable marketing results, and a superior sponsor experience:
- Interview with you to confirm objectives and draft an outline of the survey instrument, including custom survey questions.
- Creation of the survey instrument (typically between 15 and 30 questions, depending on the topic), including custom questions to impart your unique market focus and point of view.
- Administration of the survey process, including collection of survey responses from the cybersecurity panel and quality assurance. All research is based on a comprehensive online survey of cybersecurity professionals (minimum sample of 200).
- Analysis and interpretation of the survey results and application of any filters, cross tabulation, year-over-year comparisons, etc.
- Creation of report content, including research findings, charts and graphic design to bring the survey results to life in a compelling report.
- Work progress is shared with you at every milestone. This way, you can review and provide feedback on the survey and report content – until you are satisfied with the outcome.
- Publication of the final research report as part of a comprehensive marketing, PR, and social media campaign (promotion and additional content syndication, lead generation, webinar programs and infographics can be added to your custom package).
- GUARANTEE
-
We provide a unique, no-risk, money-back guarantee for report clients.
- Final invoice is not sent until the research report has been published.
- If you are not completely satisfied with the final report, we will not invoice you. No questions asked.
- You can decide when you want to be invoiced to align with your budget cycle, giving you more financial flexibility.














