
Ransomware is a serious security threat affecting companies of all sizes and industries. While the symptoms (an attack) can be extremely damaging and disruptive, the solution can be simple – proactive prevention through a heavy dose of security hygiene. Here we cover the basics of Ransomware and top tips for securing your organization against it.
What is Ransomware and how does it affect businesses
Ransomware is a type of malware that encrypts a victim’s files or blocks access to a system until a sum of money (ransom) demanded by the attacker is paid. Your systems and data can be infected by Ransomware in a variety of ways, often through phishing emails (social engineering) or drive-by downloads (compromised website) tricking unsuspected users into clicking and installing malicious files onto their machines. In addition, newer methods of ransomware targeting vulnerable web servers have also been observed as a point of entry to an organization’s network.
The global pandemic has provided the perfect breeding ground for Ransomware as remote working and mass adoption of cloud services take hold. Researchers have seen a significant increase in Ryuk ransomware, accounting for one third of all ransomware attacks since 2020 and affecting companies from healthcare providers (Universal Health Services), to law firms (Seyfarth Shaw) and online retailers (Steelcase) . Ryuk is especially dangerous because hackers use a targeted approach and often leverage several types of malware including Emotet and TrickBot malware to compromise corporate networks.
Another noticeable ransomware, Maze, works to steal the victim’s files before encrypting them as in the Canon, LG Electronics and Xerox attacks. Despite announcing the retirement of their operations in October 2020, their double extortion technique was quickly adapted and evolved by other ransomware operations such as REvil, Clop and DoppelPaymer to continue the devastation.
Ransomware prevention is not as hard as you think
As the stakes of Ransomware continue to rise, it’s all too easy to lay the blame on the victimized employees. The ugly truth is – the bad guys are just better at attacking than organizations are at defending, and the former will always have the advantage over the latter. The only way organizations can truly defend themselves against Ransomware is by preventing the infection from even entering in the first place. Instead of shiny new technologies, security leaders must refocus on bolstering their cyber hygiene to the highest standards possible, by providing their employees with the knowledge necessary to recognize and fend off phishing attacks, and the tools and processes to support proactive risk burn down.
Most successful ransomware data breaches stemmed from exploitation of known vulnerabilities (for example in third party software), or simple security failings (improper access controls, cloud misconfigurations and default vendor accounts) rather than zero-days. It’s clear that preventative security measures are far more effective in nipping the root cause in the bud, which is the very reason why ‘identify’ is recommended as the starting point in the NIST Cyber Security Framework.
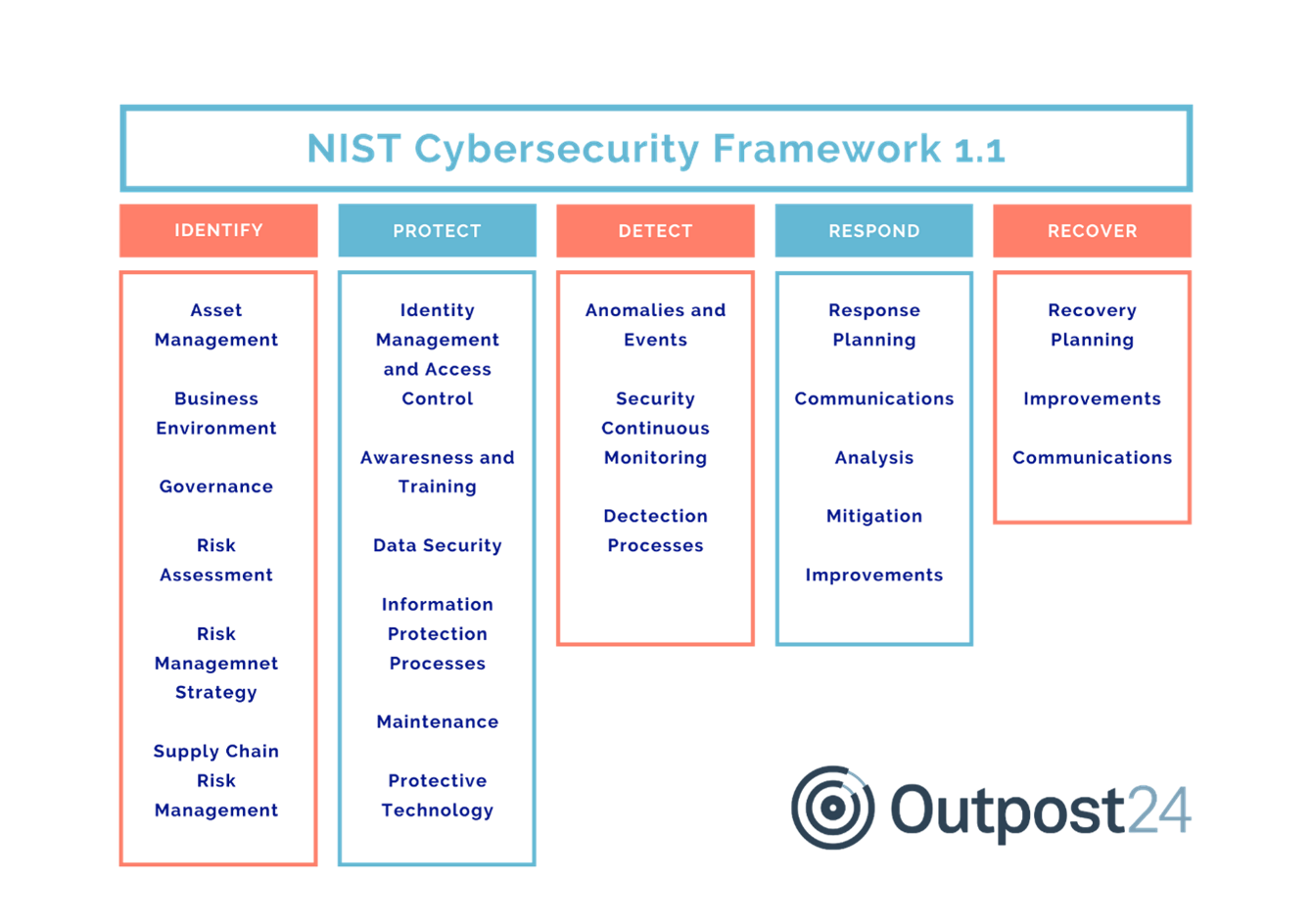
The best practice framework highlights the role of risk assessment – ‘identify’ before you can ‘protect and detect’. The pandemic paradigm shift has drastically expanded the security perimeter and attack surface. Yet many organizations simply reinforce their ‘protect & detect’ mechanism without re-assessing their risk exposure. By doing so, they spend time and resources on things that are not a risk in the first place, leaving actual risks un-protected. This is why it’s so important to start with ‘identify’ – gaining visibility of your evolving security posture and assessing where it’s weak, so that it becomes the north star of your security program. You will then have the blueprint to make better decisions, whether for vulnerability prioritization, patching cadence or new technology investment, to achieve your risk reduction goals.
A three-step plan to improve your security readiness
Proactive cyber hygiene measures are simple to implement and will instantly help improve an organization’s readiness for potential attacks.
1. Fire drill your security awareness
Businesses are having to shift their focus and embrace remote working. This has changed the security perimeter immeasurably from the safety of office firewalls to endpoints like employee laptops, increasing ransomware threats and potential system infiltration if an at-home compromise happens.
With at-home security systems being less adept than those in the office environment, it’s never been more important to turn your staff into the first line of cyber security defense. Many prevalent Ransomware and phishing attacks thrive on social engineering tactics to trick un-guarded employees into clicking on malicious links, and if downloaded, hackers can take over the victim’s computer and block access. Hence it’s essential to help employees better understand and spot these threats.
Beyond education and training, your cyber hygiene can be greatly bolstered through role play and conducting simulated phishing attacks. Red teaming exercises like these are useful to help organizations measure the security awareness level of their employees, better understand the threats and impact posed by phishing and ransomware attacks, and adjust their security program to harden high risk systems and close off previously unknown back doors.
Professional red team can help craft and orchestrate custom phishing campaigns to target employees and provide metrics on performance to ensure your business leaders have context on how a lack of security awareness can have a negative impact on your business both financially and reputationally.
2. Measure often and mitigate risks continuously
If you can’t measure it, you can’t improve it. With opportunistic hackers often basing their attacks on gaps in security defense, known vulnerabilities and unsuspecting employees, having a continuous risk assessment process is a key part of prevention. Especially for enterprises that are prone to security weakness like shadow IT and poor asset visibility.
Regular vulnerability assessment and security monitoring are essential to spot potential threats and remediate before they could become a problem. But how you do it depends on the business criticality, security maturity and technology component of your business:
- Annual testing vs continuous assessment. Not all business assets require continuous assessment, for example if they are not business critical and they do not open a path to business critical assets. At the same time, annual pen tests are not enough to secure critical infrastructure or web applications. Knowing what is critical or not in your business environment will help determine the cadence required for security testing and monitoring.
- Risk vs Vulnerabilities. For more mature organizations, the sheer amount of new vulnerabilities discovered everyday means the traditional ‘scan and patch’ approach does not work anymore. Security teams need to see beyond generic CVSS severity scores and leverage threat intelligence to prioritize patching efforts on the largest risks for the organization in order to reduce time to exposure with greater efficiency.
- Siloed vs full stack security assessment. Security is often an afterthought when adopting new technology. Even when security measures are considered, they often miss the mark due to siloed implementation. Attackers can use any security exposure in your technology stack to gain a foothold and pivot across your systems. To prevent this, organizations must move beyond siloed assessments of devices, networks, applications, data and users into ‘full stack security’ assessment to get the most complete view of their attack surface.
3. Plan for the worst hope for the best
Building security awareness and a robust cyber hygiene process from the get-go will greatly minimize your risks, but as no business is totally safe from ransomware or cyberattacks, how do you get your organization ready in the event of a Ransomware attack? Scenario based attack simulation.
Once you have invested and implemented the tools and security processes to keep attackers out, it’s important to validate that they are running and working as they should for an additional layer of security assurance. Scenario based testing, such as assumed breach attack simulation or digital footprinting will help you understand what might happen if a breach were to occur, and how far an attacker can get without being detected. It goes above and beyond narrowly-scoped pen tests to assess your preventive, detective and responsive capabilities. Just imagine if one of your remote worker’s laptop is compromised unknowingly, do you know your enterprise network is safe? Probably not.
When nothing is certain it’s important to be ready. Advanced hacking simulation will help reveal the blindspot and mature your security program based on evidence, not guess work or industry trends. Supplementing vulnerability management with this level of human intelligence could make the difference between a costly data breach and keeping your reputation intact.
Take stock of your complete attack surface today





















